Adsense High CPC Malicious WordPress Plugin in the Wild
The SiteLock SMART malware scanner detected three particular files as suspicious. Inspection of the files by the SiteLock Research Team ultimately determined that a malicious WordPress plugin was being actively hosted, used by unsuspecting site owners, and spread via YouTube.
We will detail the malware contained in the malicious plugin, reveal the relationships between the malicious plugin and other sites, and finally discuss mitigation for sites using the plugin and how to avoid such situations.
Detection and Analysis
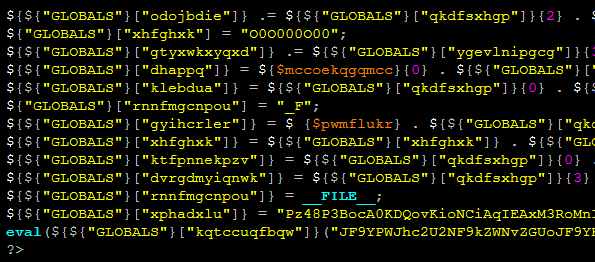
The SiteLock Research Team reviewed three encoded files marked as suspicious by the SMART malware scanner. The files were encoded much like other premium WordPress plugins using a combination of hex, GLOBALS, and base64. The files were:
/wp-content/plugins/Adsense_high_CPC.v2.0.5/cpc.php
/wp-content/plugins/Adsense_high_CPC.v2.0.5/classes/et.php
/wp-content/plugins/Adsense_high_CPC.v2.0.5/CAAQDA…Cy5Ec.php
Decoding the files found two large base64 strings, ${${“GLOBALS”}[“xphadxlu”]} and ${${“GLOBALS”}[“kqtccuqfbqw”]}. Decoding the first base64 string showed what seemed to be a less obfuscated shell with vowels substituted with the numbers 1 through 5. The second base64 string decoded to the code responsible for making the substitutions.
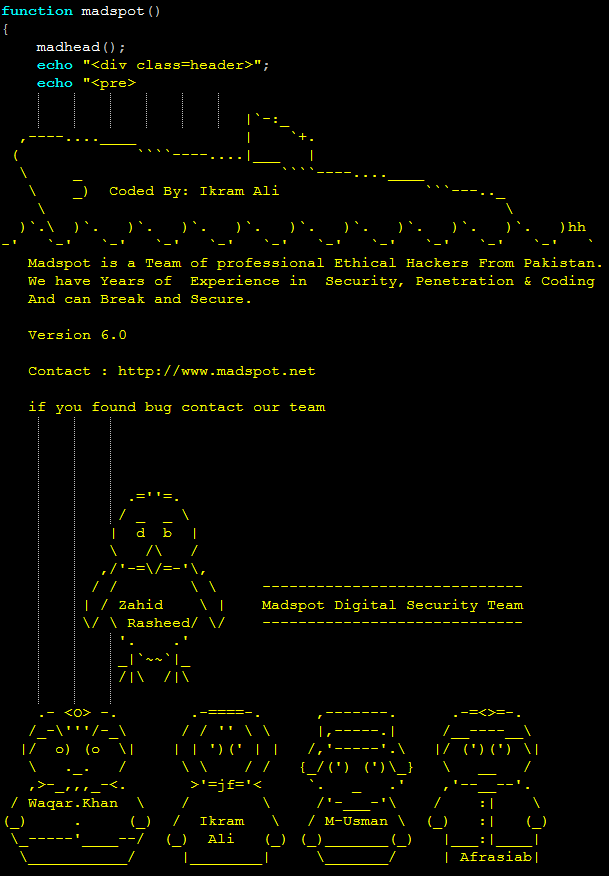
With a simple find and replace, the mostly unobfuscated code showed the three malicious files were the Madspot Security Team Shell, a modified version of the WSO shell.
With the malware verified, we needed to determine if the plugin was legitimate and infected, or if it was indeed malicious. Inspection of surrounding files showed they were taken from a legitimate WordPress plugin, Google Keyword Suggest, an indication of malicious intent though not conclusive as repackaged plugins are not unheard of. Next, we searched to find the origin of the plugin. We found a supposed support video for the plugin on YouTube which contained a link to the plugin in the description, hxxp://plugins-wordpress [dot] org/plugins/google/Adsense_high_CPC.v2.0.5/.
Following the link, we found a mirrored version of the WordPress.org plugins site and found that calling the naked domain, plugins-wordpress [dot] org redirected to wordpress.org. We downloaded the hosted zip file, Adsense_high_CPC.v2.0.5.zip, and verified the MD5s of the same three malicious files contained in the zip. Given the above findings, we determined the site and plugin were malicious and notified the host and domain registrar of the malicious activity and the site is under investigation.
The Research Team needed to verify if there was other related malware in the wild, extending the search to related sites. We found another site hosting the “support video,” though this time with a link to pluginswordpress [dot] org. Note the absence of a dash. This site simply displayed a ‘coming soon’ page. We performed subdomain analysis of the two domains and found that they shared the hosting IP of the malicious plugin site.
plugins-wordpress [dot] org. 600 IN A 160.153.16.65
mail.pluginswordpress [dot] org. 3600 IN A 160.153.16.65
We then, after analyzing the plugins-wordpress [dot] org site itself, found an image used on the site which was hosted on poststoday [dot] eu, a fake news site.
The WHOIS information for the plugins-wordpress [dot] org site, registered 2015-12-12, was private. The WHOIS information for pluginswordpress.org, registered 2015-12-01, was open, and we found an email address associated between pluginswordpress [dot] org and poststoday [dot] eu (and poststoday [dot] info). We found no other malware or malicious plugins. We were able to correlate the possible owner of the malicious sites through the hosting IP and WHOIS email address.
Mitigation
If the Adsense High CPC plugin is used on your site, remove the Adsense_high_CPC.v2.0.5 directory under /wp-content/plugins as soon as possible and have the site scanned for malware. It is also recommended to implement a web application firewall, or WAF, for the site to stop any access to malware which may remain. To prevent the unintentional use of malicious plugins, use plugins hosted at wordpress.org/plugins if possible, and vet any company behind premium plugins.


![Plugins-wordpress [dot] org](https://wpdistrict.sitelock.com/wp-content/uploads/2015/12/plugins-wordpress.org_.png)
![Poststoday [dot] eu/wp-content/uploads/2015/12/0202.jpg](https://wpdistrict.sitelock.com/wp-content/uploads/2015/12/poststoday.eu-image.png)




