
Anatomy Of A Phishing Kit
In this article, we look at a few phishing kits that were recently found in customer sites and compare their structure and complexity.
What Is A Phishing Kit?
Everyone has heard of phishing emails and phishing sites, but what exactly is a phishing ‘kit’. Put simply, a phishing kit is the set of files that are placed in a website to configure it to receive traffic and relay the data that people enter to the malicious actors. This can be as simple as a single file that does everything or as complicated as a copy of the target website with minor modifications. This article is going to explore two different phishing kits that we have found and highlight the ways in which they can be detected and avoided.
Phishing Kit – Citi Group
Overview
The phishing kit we want to highlight is one appropriately titled the Citi kit. This phishing kit is relatively small, consisting of a couple of files and a single script to send the results out. Likely, targets receive a link to http://<domain>/auth/login.html which presents the following page:

Figure 1: Phishing Site
Aside from the address and the error message this is incredibly similar to the real Citi.com site:

Figure 2: Real Site
It is easy to understand how an unsuspecting person could see the first image and just put in their credentials in the form, thinking that they were logging into Citi.com. However, even a brief pause and examination could save a lot of the future headaches that come from being phished.
Detection
First, the address bar. It is very important that you, as a consumer, know your brands. Sometimes companies will come up with a new domain for something, but if the address bar is not showing the domain name you are used to, you use a search engine to look for something like “Does domain belong to organization?” For the above example, we could search for “Does citi.com belong to Citibank” and we would find that it does. However, the domain for the site in Figure 1 does not belong to Citi and as a result, we know the login page is fake.
Another way to check any suspicions you may have because of the address bar is to look at the page source. Right click on the page, select ‘View Page Source’, and a new tab or window will be opened containing the HTML content that your browser was presented with.

Figure 3: View Page Source
Then you can search (Ctrl-F or Cmd-F) for one of the input fields of the form, ‘User ID’, for example. This will bring you to the first occurrence of that string and then you just look for the HTML form tag.

Figure 4: Page Source from Figure 1
In this case, we can see the form action (the place that the form will send any data) is set to ‘freddy/mainnet.php’ on the third line in the screenshot. Since we also see URLs pointing to explicit citi.com addresses, we now know this form is not going to submit the contents to Citi as intended. Instead, it is submitting the data to a local PHP script and, while we do not have the script itself, the structure and name are similar enough to the other phishing kit we will examine; in which we can make some assumptions about the functionality.
Behind The Scenes
Given the similarity in file structure, the ‘mainnet.php’ script in this Citi phishing kit will likely write submitted data out to files on the compromised server. Depending on the entry page, this will have username and password information (for login pages) or full name, address, and other personal information (for account creation and verification pages).
In addition to logging this data to files, these scripts also send the data via email or even via Telegram messages.
Phishing Kit – Mountain America Credit Union
Overview
This phishing kit is far more complex than the one we just reviewed. The Citi phishing kit utilized HTML pages with a single PHP script for form submission, this Mountain America phishing kit is a complex assembly of PHP scripts that are interconnected and talk back to a Command&Control (C&C) server via APIs.
From the victim’s view, the Mountain America phishing kit presents a webpage that looks very similar to the real Mountain America website, but with some notable differences.

Figure 5: Mountain America Phishing Kit

Figure 6: Real Mountain America Website
While it is missing some elements of the current site, the phishing kit is close enough that it might have been copied from a previous version of the real site.
Detection
As with the Citi phishing kit discussed earlier, detection of this kit by an end-user relies on awareness, suspicion, and curiosity. You need to be aware of the ‘normal’ website address for the brands and companies that you interact with, especially if they are financially oriented. In this case, the domain that the phishing kit was found on was a painting company’s website. This should have been sufficient enough to raise suspicions that this was not the correct site, but it may not have been obvious on mobile devices. Again, looking at the page source reveals the form submission goes to a ‘mainnet.php’ script with a session token as an argument.
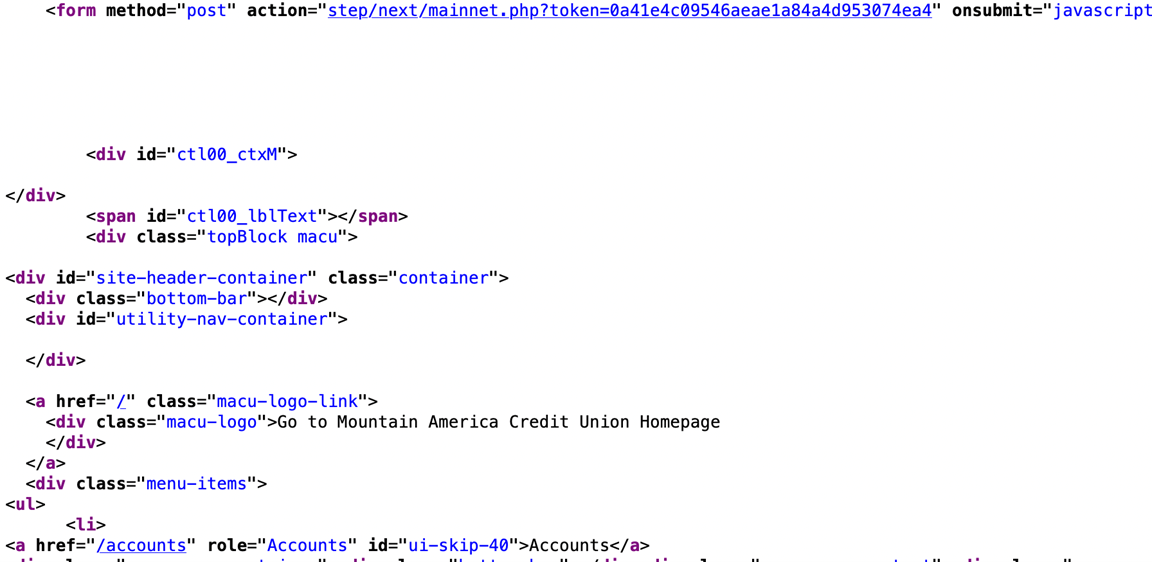
Figure 7: Phishing Kit Form Submission
Behind The Scenes
If we look at the functionality of these pages on the compromised server, the first thing that stands out is that they use a rather well-structured framework.

Figure 8: Access.php Header
The script pulls in two class files, ‘Comp.php’ and ‘Antibot.php’, performs some validation, and includes several other scripts. Of particular interest, the ‘zsec.php’ file pulls in the hacking group’s configuration, including API keys and a remote host. The rest of included scripts form a series of checks against hostnames, IP addresses, and user agents and blocking ones that are deemed unwanted. The two class files set up objects with built in functionality to perform similar blocking and application configuration.
After this header, which is present in many of the files in this kit, the file contains the HTML content displayed in the browser above. Unlike the Citi phishing kit, which relied on remote sources for images, JavaScript files, and stylesheets, this Mountain America phishing kit uses relative URIs for those same resources. This suggests they did significant reconnaissance and copying of content to create this phishing kit. A total of four of the links in the files refer to the real Mountain America Credit Union site.
In the end, the victim’s login information, card information, and personal information all get logged to various files on the compromised server, as well as being sent via Telegram messages, by the ‘mainnet.php’ script.

Figure 9: Personal Information Logging

Figure 10: Login Information Logging

Figure 11: Combined Information Logging
Summary
As you can see, phishing kits come a variety of different forms. Detecting a phishing page relies on your own suspicions and keen observation of the URLs that you are directed to. If you suspect a page is part of a phishing kit, the easiest thing to do is to close the browser window and then manually enter the website for the company you want to go to or use a bookmarked page to the company. Alternately, you can reach out to the company to ask if the domain is correct.
If you suspect that you entered your information into a phishing page, it is important to login (if you can) and change your password again. If possible, ensure that you have multi-factor authentication enabled as an additional layer of protection.
Fortunately, SiteLock can detect and remove many phishing kits and we add rules to find more every day. If you are a website owner and you suspect that your site has been compromised, and used as a phishing site, contact us today for assistance in removing the malware.
About The Author
Maarten Broekman has worked as a system administrator and systems engineer for over 25 years, primarily in the shared web-hosting space. One of the main concerns for web-hosting providers is being able to serve their customers’ websites as quickly and efficiently as possible. As a result, anything that detracts from performance needed to be examined closely and this is where his interest in malware and code analysis sprang from. For over a decade, finding, decoding, and removing malware (and automating that process) has been his primary focus.





