
Increasing Your Business’s Cyber Threat Intelligence
Authored by Sam Bocetta – Sam Bocetta is a freelance journalist specializing in U.S. diplomacy and national security, with emphases on technology trends in cyberwarfare, cyberdefense, and cryptography.
With more consumers and B2B enterprises conducting business in the cyber world, security threats are an increasing concern. While most business owners and website administrators are aware of the problem, too few have the information or resources they need to combat it. Winning the ongoing battle against cybercrime and criminals starts with understanding the nature of the threats and how to combat them.
How high is your business’ cyber threat intelligence?
What is Cyber Threat Intelligence?
Cyber threat intelligence (IQ) is having knowledge and awareness of what threatens your data integrity. In order to combat problems, cyber threat intelligence even goes beyond the knowledge that threats exist – it’s also understanding the motivations of cyber criminals and how they access systems and information. This is not to be confused with GDPR, which governs general data protection.
Threats are increasing at a pace that far exceeds the capabilities of the average website owner to keep up with them. In order for a company to have a high threat IQ, they need to take an internal and external approach to threat assessment and staff education. Internal information sources include gathering data from your system through:
* Log files
* Alerts
* Incident response reports
You or your IT security department should also keep up to date on the latest security threats from external sources like:
* Security blogs, such as Schneier on Security and Krebs on Security
* Publicly available reputation and block records, such as the US-CERT Alerts database
* Independent vendor research
Business Threat Statistics You Should Know
How real and prevalent are cyber threats? Websites experience an average of 60 attacks per day on average, according to SiteLock data. With that, 43 percent of cyberattacks target small businesses.
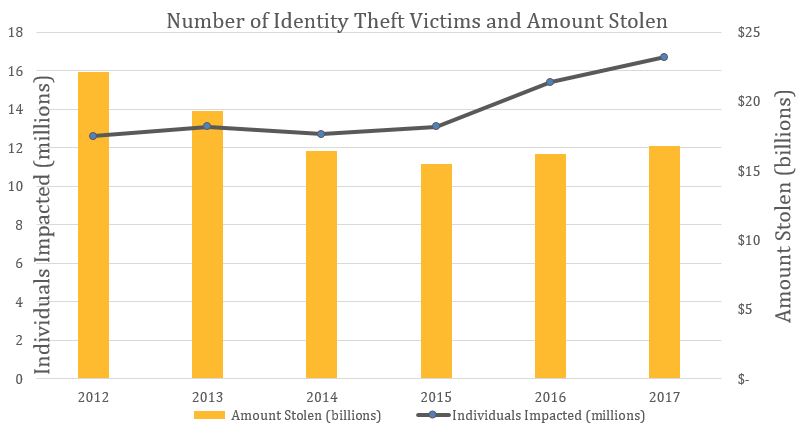
And as stated by a Harris Poll conducted in 2018, more than 60 million Americans are affected by identity theft every year. According to security industry professionals, cyber criminals will access 33 billion records per year by 2023, a dramatic increase from the reported 12 billion or so breaches in 2018.
Additionally, with the rise of mobile computing also comes an increase in related threats. Few realize that 99% of mobile malware infects systems through third-party apps, which are downloaded and installed on private and business devices millions of times per day.
In the meantime, here are concrete, proactive steps to take to protect your business and its customers.
5 Steps Toward Improving Your Business Cyber Threat Intelligence
Many computer users, website and business owners consider website cyber security as a simple, one-step process. You get a good anti-virus or anti-malware app, update, and rest is easy, right?
It’s not so simple. In order to provide comprehensive protection to your business, you need a robust system of intelligence gathering, analysis, and prevention. There are four basic types of cyber threat intelligence, each of which has its own challenges and techniques. They are:
* Tactical intelligence – the details of malicious actors’ tactics, techniques, and procedures (TTPs)
* Strategic intelligence – non-technical assessments by high-level enterprise decision makers
* Technical intelligence – tech indicators like C2 IP addresses and malware hashes
* Operational intelligence – information about specific incoming attacks that are actionable and defense protocols
While content management systems (CMS) like WordPress and Joomla! are working hard to address security concerns, it’s still incumbent upon businesses and web administrators to secure data and be aware of current cybersecurity threats.
If you’re ready to create a more robust cyber threat intelligence response, here’s a simple, five-step process that will help you reach the next level.
1. Keep everything in context
Hollywood would have us believe that every cyberattack is conducted by some shadowy figure in a faraway place. However, most website security threats are closer to home and occur through careless actions like leaving social media profiles open, creating weak passwords, or simple human error. Knowing where the most likely threats are really coming from is the first step to preventing them from harming your business.
2. Learn from the past
Although new threats are being created every day, most successful hacks are variations on old themes, like the DDoS attacks that are as old as the internet itself. Though the approaches may be new, made possible by increased access through multiple platforms, technologies, and practices like social media sharing, the basic cybercriminal MO remains the same. You, your IT security team or CIO should also analyze past breaches and leaks to determine future vulnerabilities.
3. Use comprehensive threat detection and monitoring
Most companies don’t even realize they’ve been compromised by an advanced persistent threat (APT) for nearly two months after a breach. That’s a long time for a malicious actor to have access to your databases and customer records. You can combat this by keeping website security solutions up to date, mandating virtual private network (VPN) use mandatory for local and remote workers, and being diligent about routine tasks like log monitoring
4. Dig deep
Gathering knowledge is useless unless the information you obtain is actionable. Go beyond data feeds and alerts, which simply communicate information without providing context. In order to understand relevance, you must be able to determine the what and why of the threat and how relevant or impactful it is to your enterprise now and in the future.
5. Communicate cyber threat intelligence across your whole enterprise
The second most important thing you can do after obtaining knowledge is to share it with your staff. This goes beyond making sure that IT professionals and upper management are briefed. Up to 84% of data breaches or leaks are due to carelessness from human error, and it can happen at any level of the organization. Each and every person who has access to sensitive data should be aware of the existence of threats and your company’s plans for threat prevention.
What Should You Do with Your Cyber Threat Intelligence?
Knowledge is useless if you don’t do anything productive with it. Once you’ve raised your Threat IQ, use it to create a proactive plan of action that includes:
* Strategic planning and risk management. The prevailing wisdom amongst many security professionals is that threat intel is a regular part of cybersecurity operations (and now, DevSecOps). However, it’s more than that—good intel helps security teams prioritize and manage risk. When starting my career as a network security engineer, for example, I used intelligence to determine which tickets should be read and analyzed first. Beyond ticket prioritization, teams need to know which patches should be implemented first. Ongoing data breaches or “Armageddon-level” vulnerabilities like Spectre/Meltdown would take priority over all else.
* Implementing a system of threat indicators and blocking mechanisms. What good is threat intel if not used to improve your threat detection systems and processes? Use your threat IQ reports to update your database of threat indicators, so that you’re better able to detect future threats to your network that leave the same trail. There are commercially available endpoint security solutions which handle threat indicator management.
* Creating incident response protocols. As the saying goes: “It’s not just about your IQ. It’s how, when, and where you use it.” The extent to which a company “recovers” after a cyberattack depends on how it responds to the breach – i.e. its incident response (IR). Without getting too complicated, an organization’s IR is put in place to identify and patch breaches to its network in the most time- and resource-efficient way possible. Think of IR as “damage control”. An incident response plan (IRP) is just the codified version of the IR – a manual which outlines the procedures, processes, and fixes that security analysts should implement once a breach is detected. Use the data and analyses gleaned from your Threat IQ reports to regularly update these manuals, so that your organization can bounce back after a breach, and minimize the damage done.
The Bottom Line
Advanced persistent threats (APTs) are on the rise, and new ways of invading business and personal networked systems are created every day. With increased connectivity through cloud-based computing, mobile usage, and IoT networks, your first line of defense is knowledge. This is followed closely by putting that intelligence to work through proactive prevention and threat mitigation.





