
Does Your Coffee Maker Need IoT Security?
There’s no bigger buzzword in the security world now than the ‘Internet of Things.’ The Internet of Things, or IoT, is the connectedness of everyday devices and sensors to allow the quantification and control of systems. Video doorbells alert wayward homeowners of visitors. Bluetooth fobs connect car keys to smartphones. Thermostats track heating and cooling preferences to select a tailored temperature for a homeowner. Unfortunately, the design complexity of a previously unconnected device now given intelligence and network access can lead to unforeseen issues and real-world consequences. Therefore, IoT security must be a consideration and, ideally, a foundational characteristic in their design.
Why IoT Security Matters
Without ‘baked-in’ security, IoT devices that control home automation or collect health data stored in the cloud could be vulnerable to interception, web attacks like cross site scripting and SQL injection, and attacks yet unforeseen.
We have a tangential example of IoT insecurity from the SiteLock offices we’d like to share this week. For when the manager is on travel, the research team will appropriate the keys to the coffee machine and scribble on the drink selection interface.
Infiltrating The Office Coffee Machine
The SiteLock Research Team have long yearned to hack the fancy coffee machine that management graciously provides. The machine grinds coffee fresh, makes decent espresso, and has a wide selection of hot drinks for caffiends and abstainers alike.
Step One: Reconnaissance
We saw no Ethernet cable from the machine and verified with IT it had no wireless capabilities. Physical access it was. We tried numerous ‘secret’ button presses on the touch screen to try to bring up an administrative interface with no luck. We would have to open up the machine.
We could have simply asked for keys and got them. However, we decided to maximize fun and surprise, and perform the hack while the boss was away.
Step Two: Gaining Access
With keys in hand, we opened the machine and were greeted with a service menu and Login button. The Login button brought up a 10-key interface looking for a four-digit passcode. Seconds later ‘1111’ brought us to the Level 1 menu.
Level 1 provided machine info though not what we wanted — access to images. We correlated the passcode of ‘1111’ to Level 1 and tried to log in again with ‘2222’ to get the Level 2 menu. ‘2222’ didn’t work, though ‘3333’ did. ‘4444’ and ‘6666’ brought us to respective menus, each with the previous menu’s capabilities and more sensitive actions added on, like payment and temperature settings.
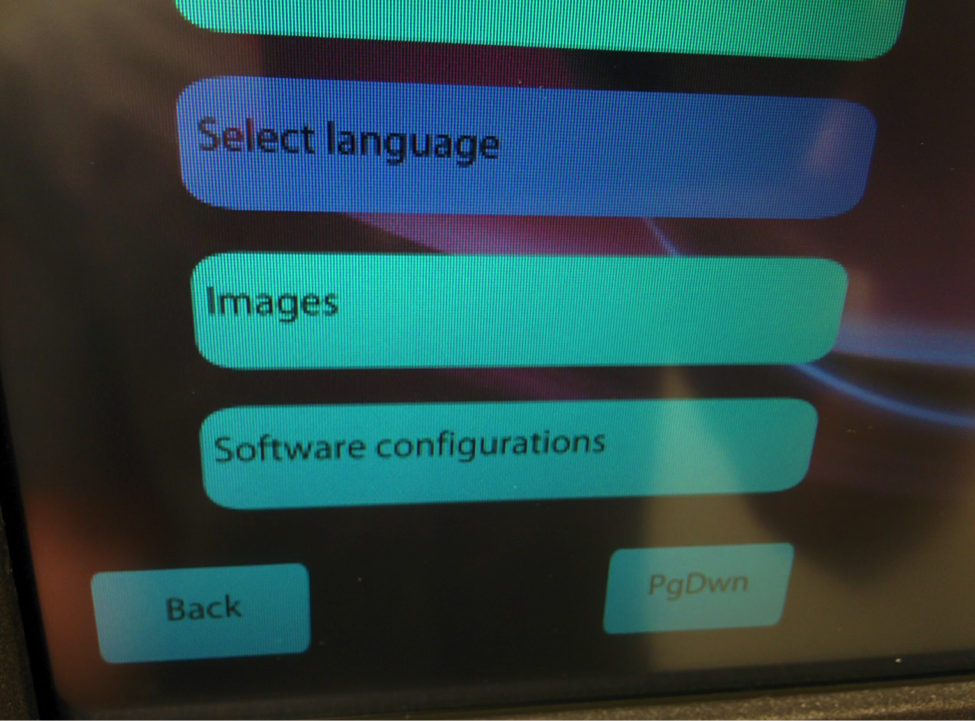
Level 2 Menu
Level 2 gave us what we needed, the ‘Images’ menu. With it we were able to add an image from a mounted flash memory drive via the internal USB port. Mission accomplished.

Haxed by SiteLock
Step Three: Digging Deeper
We decided to dig a bit deeper and download the config file via the ‘Software configurations’ menu. With config in hand we ran a simple strings on the file and found all of the passcodes in plaintext at the end of the file.
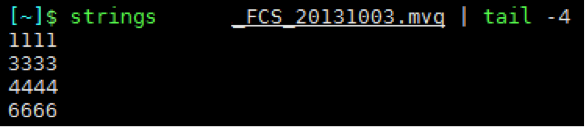
Strings Output
Conclusion
This doesn’t seem like an Internet of Things device at all, let alone a hack on one. Until you find out the manufacturer offers wired and wireless communications and telemetry solutions for this and other models. If this device were accessible via the Internet, a hacker could forgo the necessity for physically taking keys to the device, and instead use network access and a browser or command prompt. The coffee machine becomes an IoT device that might be hacked with less effort and lower rate of detection.
It’s likely many readers already have internet-connected devices in their homes and on their wrists. Manufacturers are sure to improve IoT security by design in devices. Until that time, consider what data your personal IoT devices collect, where they connect to, and what data could be transmitted. If firmware or other device updates are available, apply the updates as soon as possible.
Will there be a perfect, secure world where IoT devices adapt your surroundings in real-time based on your location, preferences, and well-being? Not yet. Though the scenario is more attainable every day. Will SiteLock scanners, like INFINITY, begin to scan IoT devices like they do websites now? Time will tell.
Want to read more IoT security news? Check out our article on the Wikileaks hack that uncovered CIA research exploiting vulnerabilities on internet-connected devices.





