
Ask a Security Professional: DDoS Attacks — Part One: DoS vs DDoS
There’s a lot of buzz going around in many online communities concerning the recent distributed denial of service (DDoS) attacks the world has witnessed. In many of my own circles I’m often the only security guy in the room so I end up fielding a lot of questions, the most common of which is, “how do they do this stuff?!” In this series, I’ll be explaining the anatomy of D/DoS attacks and the practical weaponization of regular computers.
In Part One we’re going to look at the differences between a denial of service (DoS) and a distributed denial of service (DDoS) attack. This can be an especially important distinction, because while some security services/applications may protect against one, the vast majority provide little to no protection against the other.
The Anatomy of a Denial of Service (DoS) Attack
Denial of service attacks is a broad category characterized by the specific intent to deny legitimate traffic access to a specific service, hence being dubbed denial-of-service. When the term ‘DoS’ with a single ‘D’ is used as opposed to ‘DDoS’, that is typically denoting that the attack is carried out by a single computer through a single internet connection with the intent to disrupt a web service by either exploiting a vulnerability at the target machine or network, or by overwhelming the target machine or network with a flood of data transmissions that exceed their processing capability. In the case of a website, this results in the site becoming unreachable to normal visitors, most often because the website server will begin to fail to respond within a reasonable amount of time while being saturated with junk data from the attacker.

The Anatomy of a Distributed Denial of Service (DDoS) Attack
Distributed denial of service (DDoS) attacks use aim to increase the strength of a DoS attack by involving multiple computers and internet connections. Where a single-computer DoS attack is limited by the computational power and network bandwidth available from its point of origin, DDoS attacks often involve hundreds or thousands of machines and connections from across the world to leverage immense resources against a target. This can mean the difference in power between a slingshot and a howitzer.

Photo credit US Army Spc. Lucas T. Swihart
In most of the large-scale cases we see these days, coordinating a DDoS attack starts with building a botnet, a network of computers amassed most often from malware-infected personal computers being remotely-controlled (dubbed zombies), turning innocent bystanders into involuntary assailants in the attack. Once a sufficient number of computers have been collected into the botnet through infection by purpose-built malware, the hacker-turned-botmaster is able to launch an effective DDoS attack. At SiteLock, we regularly document cases where WordPress websites have been infected with malware with the apparent purpose of infecting visitors with malware that will allow the hacker to control the visitor’s computer as part of the expansion of a botnet. In turn, both the infected website server and infected visitor’s machine can be leveraged as zombies in an attack. Many botmasters offer DDoS-for-hire services where customers can inexpensively rent the botmaster’s botnet at hourly rates to besiege a target server, opening access to a devastating DDoS arsenal to anyone with a Paypal account or a little bitcoin.
DDoS-for-hire sites often resemble legitimate ecommerce websites.
Not all DDoS attacks are orchestrated through the use of unwilling participants. As cyber warfare has evolved, we’ve seen the introduction of volunteer botnets where those willing to participate in attacks need simply download an application to their computer to join the party. Voluntary botnets have seen use in such notable attacks as Operation Payback and Operation Megaupload where in each case, a group of activists operating under the Anonymous moniker volunteered their computational resources to large-scale DDoS attacks through DDoS tools such as Low Orbit Ion Cannon (LOIC) or its more recent sibling High Orbit Ion Cannon (HOIC).
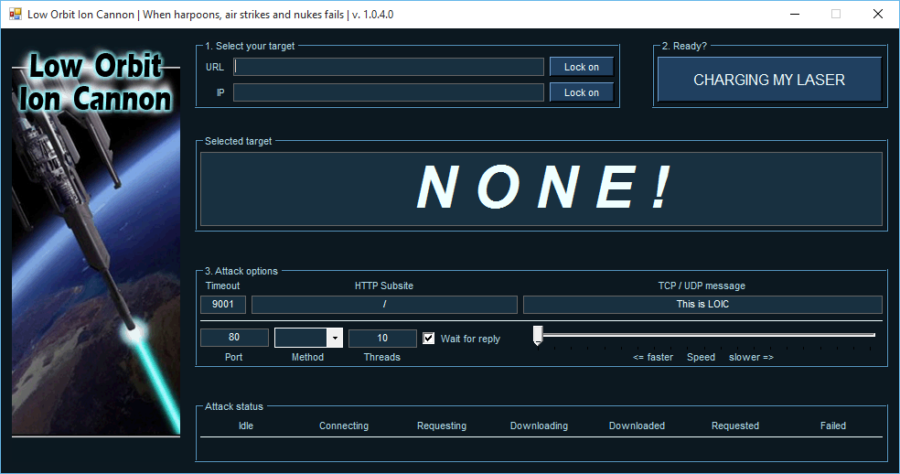
“CHARGING MY LASER” in open-source DDoS tool “Low Orbit Ion Cannon” (LOIC).
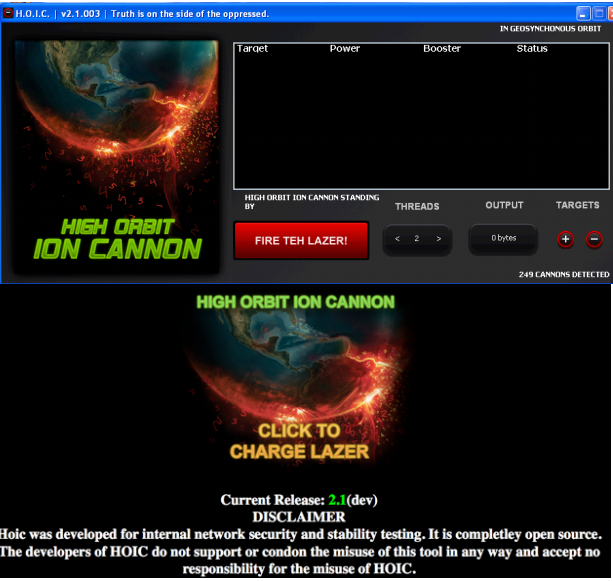
“CHARGE LAZER” if you prefer, using newer DDoS tool High Orbit Ion Cannon (HOIC).
DDoS attacks have grown in both volume and frequency in 2016, implying that the trend is only going to continue to increase through 2017. Larger and larger attacks are being seen across the world, and now with the onset of the internet of things (IoT), there are a whole new breed of devices to enslave and new security considerations to ponder. However, the fact remains that the majority of botnet slave computers are infected by compromised websites, many of which were originally legitimate. With SiteLock® TrueShield™ you can protect your WordPress site and visitors from infection, and defend against any DDoS attacks that may come your way.
Have a question for our security professionals or a topic that you would like us to write about? Message @SiteLock and use the #AskSecPro tag!





