
Ask A Security Pro: DDoS Attacks — Part 3: Protocol-Based Attacks
Continuing our #AskSecPro DDoS series where we last discussed Application Layer Attacks, today we’ll focus on some of the most popular protocol-based DDoS attacks we’ve seen hit our customers’ web application firewall, SiteLock TrueShield™, over the years. TrueShield™ is SiteLock’s distributed cloud-based web application firewall (WAF) with the capability of defending against attacks across layers 3, 4, and 7.
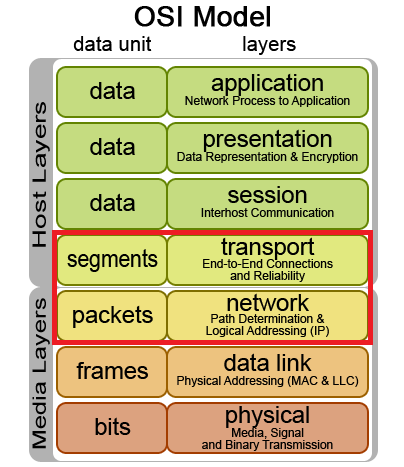
Protocol-Based DDoS Attacks
Protocol-Based Attacks target Layers 3 and 4 of the OSI model in the target’s infrastructure. Rather than being limited to exclusively targeting the web server itself, these attacks may target intermediate resources such as firewall appliances, ironically utilizing the appliance as an instrument of denial for legitimate traffic by consuming its computational resources until it is not able to process additional data.

Protocol-Based Attacks are measured in magnitude by packets per second (pps).
If you haven’t already heard of it, one of the most historically-relevant approaches to a protocol-based denial of service is the infamous Ping of Death, which exploits another generic principle in the TCP/IP protocol — packets. Packets are the units of data carried across networks and form a fundamental part of how data is communicated across the internet. During communication, large amounts of data are broken into little bite-sized portions for consumption by the computers involved to make it easier to process. You’re probably using the protocol IPv4 to read this article right now which is still the most widely-used internet protocol today, these units of data have an expected length of about 64 bytes including the IP header. The Ping of Death attack seeks to confuse and potentially crash the target server by sending malformed or oversized packets, which when interpreted by the server, may cause an anomaly called a buffer overflow where data exceeds an expected boundary and can cause a crash. Game over!
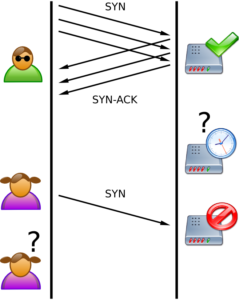
Another one of the most popular methods for protocol-based DDoS attacks is the SYN Flood. Normally when a user visits a website, the visitor requests a a connect by sending a synchronize (SYN) request to the website’s server, which once accepted is acknowledged (SYN-ACK) by the web server, and in turn acknowledged (ACK) by the visitor. This routine process of a three-way handshake is commonly abbreviated as simply SYN, SYN-ACK, ACK, which is the foundation of establishing a TCP connection between as website and a visitor. A SYN Flood exploits this handshake process by sending the initial SYN request but never responding with a SYN-ACK, which essentially prompts the target server to continue to wait for the ACK-SYN response it’s expecting. Web server have a finite number of connections they’re able to maintain, so by saturating the server with enough of these half-open connections, the server will eventually be unable to open connections to present website content to legitimate visitors. Game over!
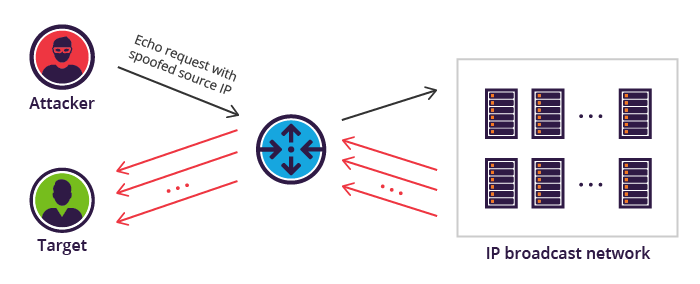
On the more colorful side of DDoS is the the classic Smurf DDoS attack, named after the DDoS.Smurf malware found on the infected zombie machines that form the botnets used in the attack. The Smurf DDoS attack uses an ICMP echo request (ping) flood which is amplified by spoofing the address of the target server when contacting another third-party server with the request, prompting the third-party server to deliver the response to the request to the target server, unintentionally becoming a weapon against the target. Adversaries typically hoist in vast quantities of these third-party servers to increase the effectiveness of the DDoS attack.
We’ve seen a variety of ways that adversaries can utilize innocent third parties as both zombies and as amplification methods, inheriting their collective resources and thus their firepower. It is no longer practical to expect that relying solely on an endpoint solution will protect you against network or other protocol-based attacks. The best solution is to use a distributed cloud-based web application firewall (WAF), such as SiteLock TrueShield™, which protects against DDoS attacks across layers 3, 4, and 7. Learn more about how SiteLock can help you defend against DDoS attacks.
In our next episode of Ask a Security Professional, we’ll be talking about Volumetric DDoS Attacks. Have a question for our security professionals or a topic that you would like us to write about? Message @SiteLock and use the #AskSecPro tag!





