
Ask A Security Pro: Firewall Series – Part 3: Stateless VS Stateful
In Part Three of our firewall series, we’re drilling down into some of the mechanisms used in firewalls, namely the progression from stateless to stateful packet filtering. First, packet filtering is the action of inspecting the traffic traversing the firewall’s network to determine if the traffic is meeting the firewall’s security policy. Traffic conforming to the firewall’s security policy is allowed to proceed, while traffic not meeting the policy (e.g. a malicious attempt) is blocked.
Stateless Packet Filtering
Packet filtering in firewalls initially consisted of analyzing each packet for its compliance against a firewall’s security policy without any regard for context in the form of any existing data streams (i.e. connection “state”). Stateless packet filtering is capable of evaluating risk based on the remote user’s IP address in the form of IP reputation, where the IP address is compared against databases of known bad IPs, as well as evaluations based on port and protocol. However, without taking the traffic’s context into account and instead inspecting each packet individually, the stateless firewall has no method for preventing unsolicited connections. This can make the firewall more vulnerable to certain types of attacks by not discriminating traffic, whether or not a prior connection exists.
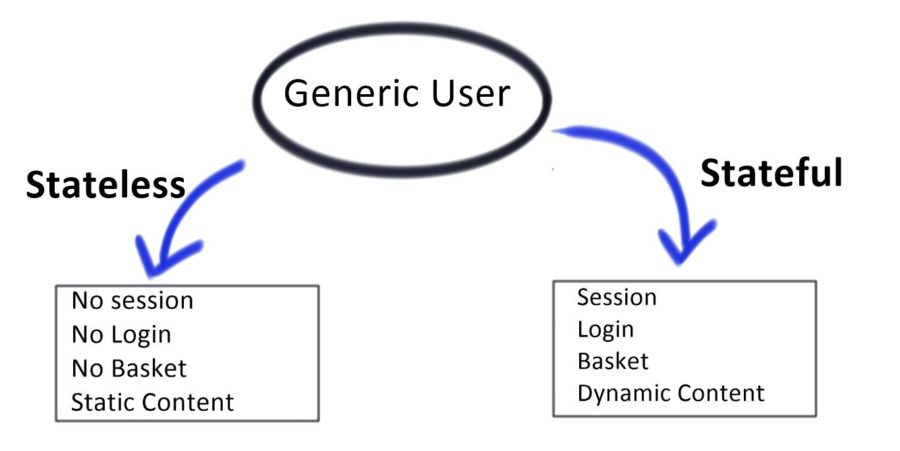
Stateful Packet Filtering
Most modern network firewalls utilize stateful packet filtering. In contrast to stateless packet filtering, stateful firewalls acknowledge the context of traffic by keeping track of the state of each active connection. By tracking the context of the traffic traversing the firewall’s network, the firewall is more able to establish patterns of lower and higher risk to better recognize the differences between malicious and legitimate traffic. As part of tracking data streams, new connections must perform a handshake with the firewall before being moved into the list of “established” connections. The handshake process at the beginning of the connection significantly increases the computational power required to form a new connection, which we often see exploited in the form of distributed denial-of-service (DDoS) attacks. The increased vulnerability to DDoS introduced through the handshake process is often mitigated by distributing network traffic across a larger number of firewall appliances, often as cloud-based services, such as SiteLock® TrueShieldTM.
Have a question for our security professionals or a topic that you would like us to write about? Message @SiteLock and use the #AskSecPro tag!





