SiteLock Research Team Uncovers WordPress Plugin Vulnerability
The SiteLock Research Team will have many firsts as it develops. This week we’ll discuss the first reported and patched vulnerability the team found, a minor cross-site scripting vulnerability in Testimonial Slider.
The team has been working on putting together a new vulnerability research process. During the creation of this process, we tested a not-so-randomly chosen WordPress plugin, Testimonial Slider. Developed by SliderVilla.com, it displays customer testimonials in a responsive slider and has over 10,000 installs. We chose Testimonial Slider for no other reason than it was a slider plugin after the recent Revolution Slider exploit.
What Does Testimonial Slider Do?
Testimonial Slider, developed by SliderVilla.com, displays customer testimonials in a responsive slider and has over 10,000 installs. We analyzed version 1.2.1 using SiteLock TrueCode and manual analysis.
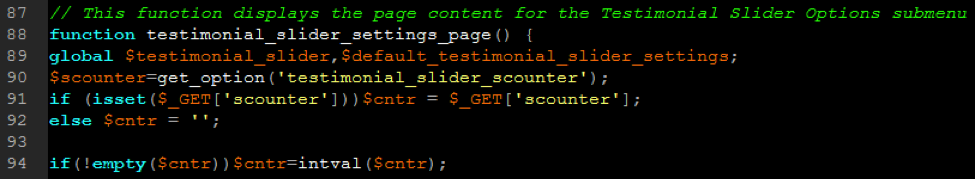
The vulnerability was an authenticated, reflective cross-site scripting, or XSS, vuln. If you haven’t heard of XSS before, it is a vulnerability in a website or web application code, that allows bad actors to inject their own code into a web page. TrueCode pointed us to the possible vulnerability in Testimonial Slider’s settings.php file, specifically line 203, where a variable named $curr is located. In the image below, you can see that this variable is echoed out in the page’s source code.
TrueCode Output
Tracking Down The Vulnerability
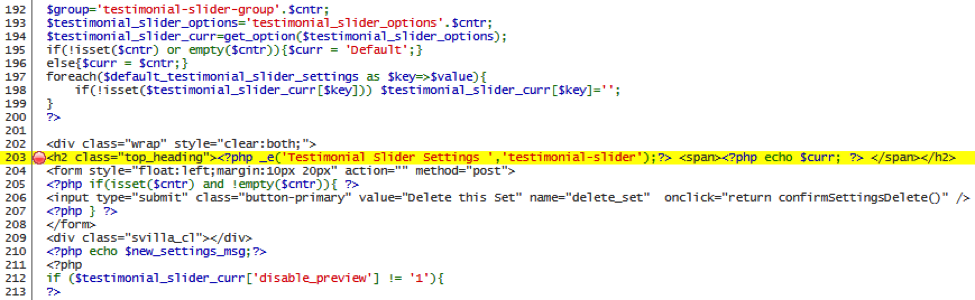
We backed through the code to find where $curr was set, which was in lines 195 and 196 where it was set to ‘Default’ if another variable, $cntr, was empty, or simply $cntr if not.
The payoff came in lines 91 and 92 of the code, where the value of the $cntr variable was set.
if ( isset($_GET['scounter']))$cntr= $_GET['scounter'];
The value of a $_GET variable is passed through the page URL. Whatever the value of $_GET[‘scounter’] was set to, its value was assigned to $cntr and subsequently $curr, where the reflective XSS vulnerability was.
Settings.php Before Fix
Proof Of Concept
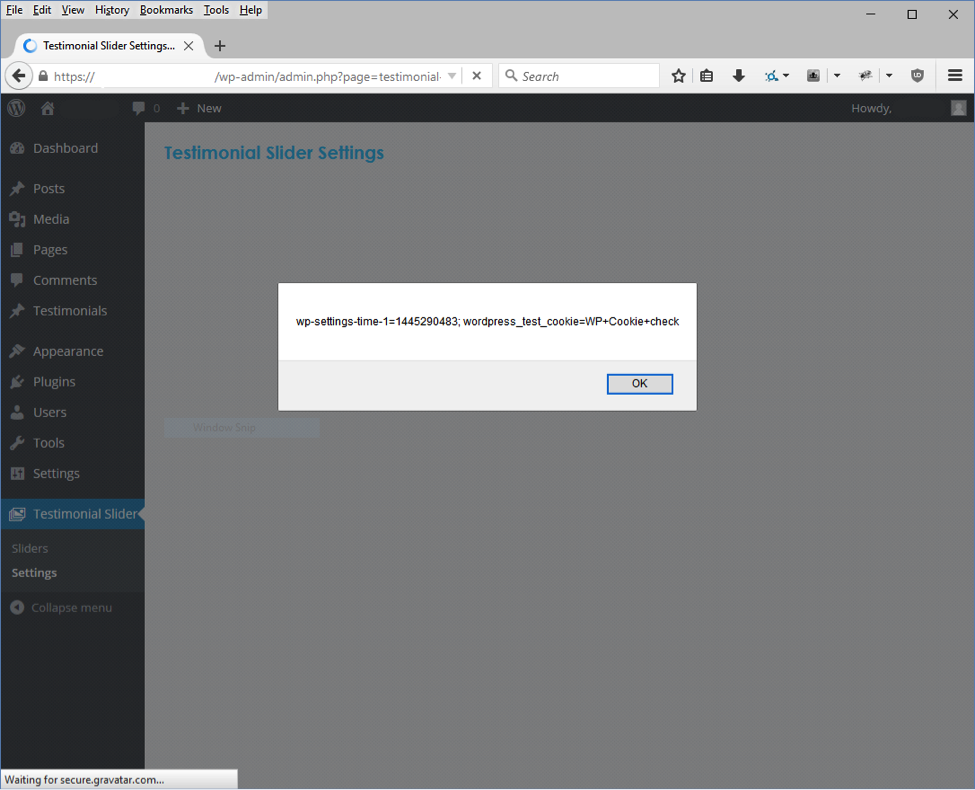
To demonstrate that the XSS vulnerability existed, we simply needed to pass the XSS string in the scounter GET variable. The proof of concept would be a JavaScript alert box showing a document cookie message.
Quick Turnaround By SliderVilla
We reported the vulnerability to the developer and it was fixed within 10 days:
- 19 Oct 2015 – Notified developer, http://slidervilla.freshdesk.c...
- 20 Oct 2015 – Developer responded, ‘We will fix this issue on priority and release an update soon.’
- 30 Oct 2015 – Developer released version 1.2.2, ‘Fix – Input validation of s-counter on admin panel’
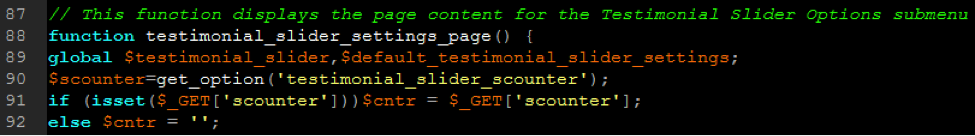
To fix the vulnerability, the developer added code which set $cntr to the intval of $cntr, which returns 0 if strings are passed.
Conclusion
We would like to thank SliderVilla.com for their responsiveness. As the Research Team grows and processes developed, the team will have more time to analyze more WordPress plugins and eventually include plugins for other content management systems.
The code analysis tool that the SiteLock Research team used to help uncover the vulnerability was TrueCode Static Application Security Testing. Visit our website or call 855-378-6200 to talk with a website security consultant about putting together a custom package containing TrueCode SAST.